Overview
Circle’s Distributed Multi-Factor Authentication eliminates the use of any central certificate authority, credentials or cloud-based identity databases, with all operations conducted with an AES 256 encrypted Circle. There are multiple ways that this capability can be applied to different use cases and needs. This article describes its use as a separate and stand-alone method of direct peer-to-peer authentication between end users.
Description
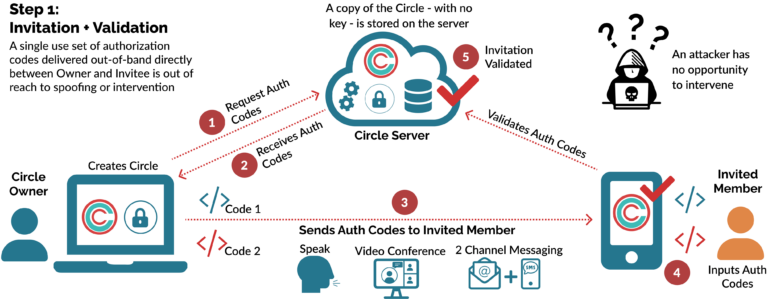
A Circle is created by a Circle Owner - the Circle initially exists with the Circle Owner as its only member. The Circle Owner can then invite others into that Circle. When a Circle Owner wants to add Members to the Circle they add them by inviting and authenticating them. The Circle Owner shares two pieces of information with the Member invitee:
- Code 1 (Invitation ID)
- Code 2 (Authorization Code)
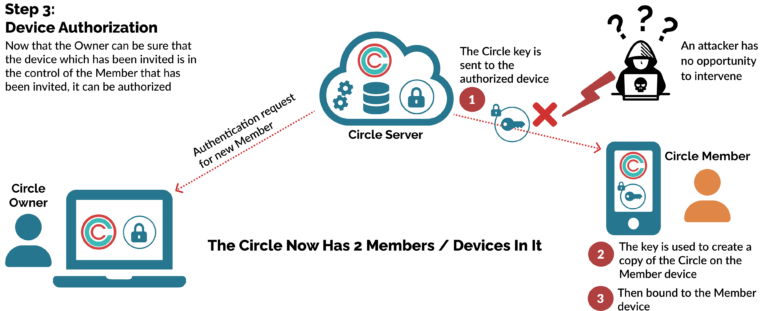
This enables the Circle Owner to invite and authorize the devices of Circle Members that are being invited. Once authorized, the unique AES 256 key for the Circle or Digital Capsule / Topic that has been created is shared using standard secure PKI exchange. When this process is completed, all devices in the Circle now have the same unique key - and no other devices or Cloud servers in the world do. The codes can only be used once, and there is no record or database - other than within the Circle - of user data, metadata.
Demo
To see an example of Distributed Multi-Factor Authentication in action, please see:
This is a simple demonstration of secure exchange of data between users and devices that create a Circle on the fly, with zero attack surface in the cloud. For an explanation of how the demo works, please see:
Security and Privacy Advantages
This method of authentication has multiple advantages for end user security and privacy.
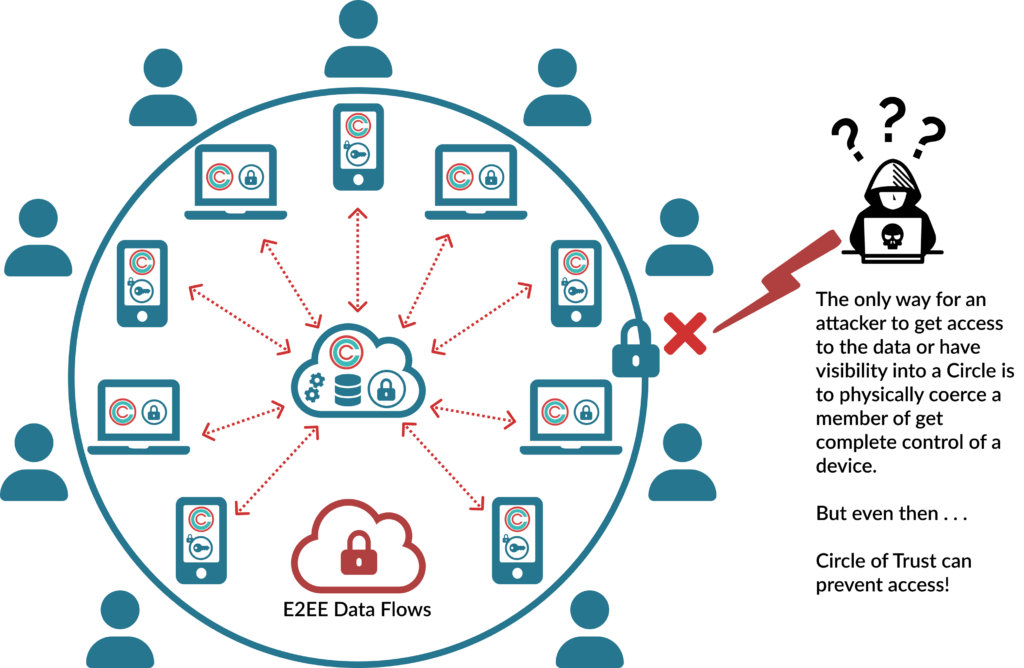
- There is no cloud server containing credentials, user identities, or otherwise - no central authority of any kind.
- All data and meta-data about the users in each Circle are contained within the Circle.
- Therefore, there is no point of attack to capture, spoof, impersonate, steal or otherwise break the authentication.
- To get inside the Circle, the attacker must be personally invited and authenticated by the Circle Owner.
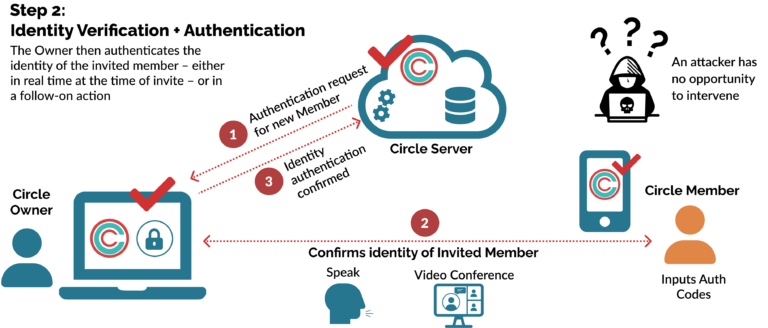
Developers can design, configure and deploy this method to varying degrees of rigor. In particular, to maximize security it is important to add steps and checks the enforce identity verification as part of the process of authentication. Developers may be interested in the Circle-of-Trust as a turn-key solution in this area, which provides a method of distributed human-in-the-loop identity verification that is cryptographically fused to device authorization.
Diagrams
These diagrams present a step-by-step outline of how this can be implemented in one possible design.
Step 1: Invitation + Validation
Step 2: Identity Verification + Authentication
Step 3: Device Authorization
A Secure, Private Circle is Formed
A Circle is a secure virtual private network between a group of devices that is set up by a Circle Owner through this hybrid P2P authentication process.
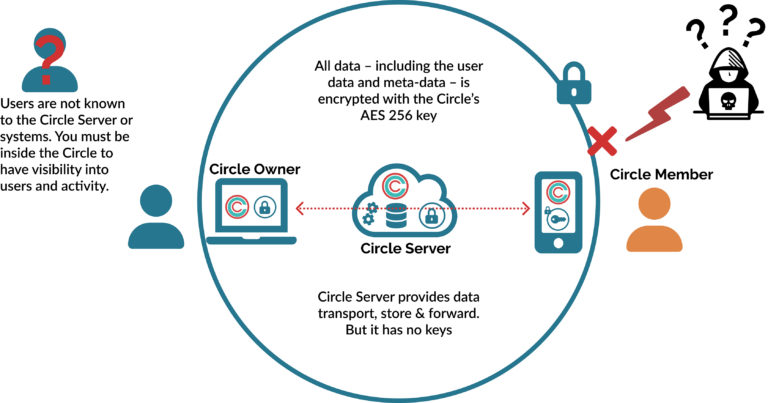
With No Limits on Size or Duration
Once a Circle is created through this method of distributed multi-factor authentication, the members/devices in can communicate and exchange data with complete security and privacy. Since there is a single AES key for each Circle (or secure capsule within a Circle), there is no limit on the number of members, the amount of data or duration of a Circle. Circle handles rekeying and other operations to protect very large and long-lasting Circles.