Circle is a transformative data security platform built on a next-gen decentralized architecture that secures Access and Data for third-party applications with no compromise for user experience. Circle delivers its breakthrough architecture as a REST API to enable developers, IT teams and DevSecOps to incorporate and support fundamentally strong security in these areas with:
- Far less complexity - meaning developers will use it; and
- Greatly improved user experience - meaning users will use it.
Circle API does not seek to replace the Cloud - it is a powerful and critical infrastructure driving the success of modern application development and digital infrastructure. Rather, it addresses some of the fundamental weaknesses of current cloud-native architectures in a way that enables the efficiencies and power of the cloud to be preserved while radically improving security.
Circle's approach to threat prevention
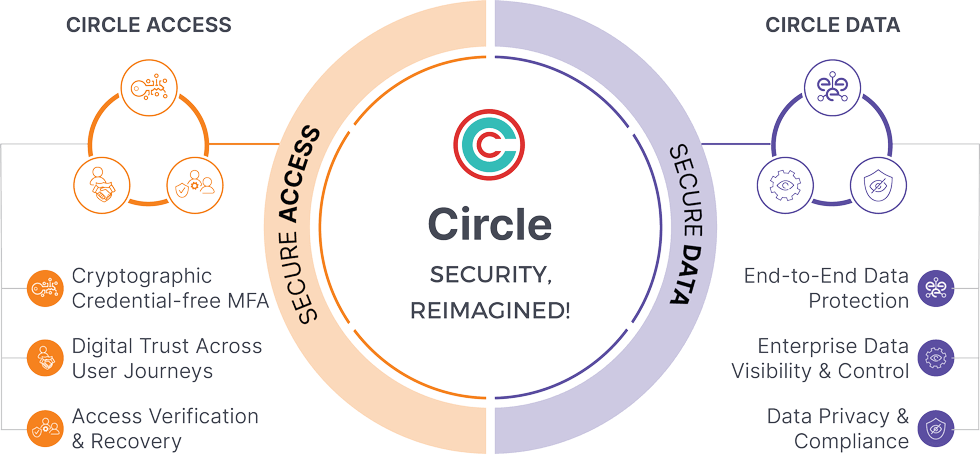
Our approach to Threat Prevention consists of two major components.
- Threat prevention by securing access (Circle Access)
- Decentralized and credential free MFA for authenticating user across systems
- Zero trust principles with continuous authentication and verification enabling digital trust
- Strict governance policies with customizability for business friendly implementation
- Threat prevention by securing data (Circle Data)
- Encrypting data at rest and in motion without compromising scalability and security
- Giving data owners the ability to restrict data visibility and access to only authorized users in "Secure Capsules" on authorized end point devices.
- Enabling default adherence to compliance standards of HIPPA, CCPA , GDPR
Our implementation strategy
You can deploy the Circle platform and APIs as stand-alone capabilities or as a comprehensive solution to deliver uncompromising access and data security.
- Deployable at both developer and enterprise level
- Easy onboarding and frictionless integration with multiple systems
- Fast implementation with API based integration
- Access protection through authenticator app - more secure than SMS based authentication
- Flexibility of integration at multiple levels of security policies
Dual Integration Options
Generally, there are two easy ways to rapidly integrate Circle APIs with low code/no code for both web and device native applications. The specific options and APIs depend on which capabilities you choose to implement.
Circle Access
REST API
- Easy & Rapid REST implementation
- Effortless Maintenance
This is a traditional REST API which calls to the Circle Access server in the Cloud. As you will learn, that server has some unusual characteristics in that it has no decrypted data and we know nothing about the endpoint devices and users that authenticate with it.
Modules
- Modules available for various integrations to minimize effort and maximize functionality.
Circle Access has 3 UX options which can be implemented together or separately.
- Circle Access Lite
- No install, leverages HTML5.
- Circle Access Mobile
- A mobile authenticator app like no other, protecting both Access and Data.
- Circle Access Desktop
- Completely frictionless and invisible.
- Requires installation of a thin client (Circle Access Desktop)
We recommend that you implement all 3 options and let your users determine what is best - which will often depend on their use case and different device platforms they are using.
Circle Data
REST API
- Easy & Rapid REST implementation
- Download of thin client (Circle Access Desktop)
- Effortless Maintenance
As you will learn, Circle Data REST API has some unique characteristics in that it calls to our thin agent, Circle Service, as a localhost running on the endpoint device.
SDK & Libraries
- Lightweight libraries
- Inline & embedded implementation (Circle Service thin agent included in your own software application)
- Fully Integrated with your application workflows
Circle API products
Since Circle can do so many different things, we found in our engagement with developers and partners in our early access program that it is helpful to structure our offering, and the supporting content for integration, implementation and development in the following packages. These group together and match areas of functionality in the API to use cases that developers and end users want and can be easily slotted and integrated to meet specific needs within the SMB market and enterprise IT infrastructure.
Circle Access
Circle Access enforces Zero Trust Access Security to your data and resources with a frictionless implementation that radically improves both UX and security.
Circle Access API has the following 3 primary capabilities that we are currently focused on productizing and supporting. There are many other capabilities that we know of, and you have a particular use case or need that is not presented here, please be sure to contact us for a free consultation.
Frictionless Cryptographic Credential-free MFA
Passwords are a disaster waiting to happen, and traditional MFA relies on passwords and other weak factors that cannot counter the sophistication of attackers. Remote working is the new normal and demands that companies ensure the identity of the user behind every device. With Circle Access, you can implement our breakthrough Zero Trust Access Security solution or add it your existing MFA in 30 minutes or less.
Digital Trust across User Journeys
With Circle Access, you can enable continuous cryptographic authentication and biometric identity verification so that you can trust the device and know the user to prevent fraud in digital actions, user journeys, and transactions.
Access Verification and Recovery
All traditional MFA is just a best guess that the user on the device is the user you have authorized. Cloud infrastructure and communications channels are both vulnerable. For many use cases involving access to critical, valuable resources, this simply is not good enough. That's why we created Circle-of-Trust, which powers a step-up escalation to a breakthrough Zero Trust unspoofable human-in-the-loop identity verification to absolutely protect your most sensitive digital resources, actions and powers.
Circle Data
In today's world of ever increasing sophistication and volume of threats, even bullet proof authentication is not sufficient. At the very least, your most critical and sensitive data needs to be protected at rest and at transit. Traditional data security platforms categorize data into sections and then provide dedicated encryptions to specific data sets which in a cloud infrastructure is vulnerable. That's why we created Circle Data.
Circle extends Zero Trust security to data itself
With Circle, the same encryption keys used to authenticate identities and their actions can be used to secure data end-to-end. Circle encrypts data at rest and in transit enabling collaboration with the keys to encrypt and unlock the data only available on authorized endpoint devices. This enables you to extend Zero Trust Security principles to your most critical and important data itself with flexible controls and ease-of-use of a frictionless and invisible UX. You can take advantage of our integrations with popular applications like Microsoft SharePoint and Office 365, with many more to come!
Circle Data API has the following 3 primary capabilities that we are currently focused on productizing and supporting. There are many other capabilities that we know of, and you have a particular use case or need that is not presented here, please be sure to contact us for a free consultation.
End-to-End Data Protection
With Circle Data, you can safeguard your data on endpoint devices and in Cloud easily by leveraging "Circles" (a group of devices defined by possession of a unique AES 256 key) and "Secure Capsules" (folders or containers of encrypted data). As an application developer, one of the most interesting characteristics of this is the ability to store data on the endpoint device that is accessible only to either:
- Your Web server.
- An affiliated trusted server - such as an IAM platform (e.g. ForgeRock, Okta) or Authentication server (e.g. Auth0); or
- Your application software on the endpoint device.
The data in this Circle is not available to the end user - so they can't breach it - or any malicious attackers that might get onto the device. It is also not transmitted to or readable on your cloud servers, so they cannot be a source of breach. Very useful!
Enterprise Data Visibility & Control
As noted above, Circle Data creates AES 256 encrypted secure capsules that can contain any type and amount of data, but which is controlled by the data owner. This same capability can be leveraged to enable organizations to protect their data in a BYOD model without impinging on employees' privacy.
Data Privacy and Compliance
Ever more strict regulations are requiring general, or industry specific data privacy, with the costs in fines and legal liability for failure often reaching millions of dollars. Circle's privacy-by-right architecture enables application developers and enterprises to maintain privacy and compliance simultaneously, meeting all the requirements of HIPAA, GDPR, CCPA, PIPEDA, PSD2 and more. With Circle, NOBODY other than the Data Owner has access to their data - or metadata - EVER.
Unique Characteristics of Circle Data API's Hybrid Cloud P2P Architecture
There are four characteristics of Circle Data's architecture that are particularly important to its security, utility and uniqueness. These are also different in some important ways from typical REST APIs which developers leverage for cloud applications, so understanding these can be helpful to both implementing and integrating Circle as well as thinking of innovative ways that it can be used.
- The Circle software service installed on the device performs as a local host web service on the endpoint device. After the initial set-up, the system web server has no role in authentication and no access to any data that is used to perform it. All communications and actions are performed only between the application web server and the software service running on the local device.
- Encryption keys are created and stored on the endpoint device and are never shared with any web server. The Web Server itself never receives or stores a copy of the key - the information stored in the secure capsule can only be requested by the Web Server, and then decrypted locally on the device and transmitted to the web application server for authentication purposes. The Circle platform's web server also never receives or stores any keys, nor can it request or in any way access information that is stored in secure capsules.
- It creates AES 256 encrypted Secure Capsules. which can be bound to the device upon which they are authorized, but also can be uniquely bound to the human or machine user they are intended to protect. Secure capsule can be securely replicated and synchronized to other devices controlled by the same end user through a peer-to-peer process of invitation and authentication. This enables a single end user to replicate and control the same Secure Capsules across multiple devices, browsers and contexts.
- There is no centralized certificate authority or credentialing system required. The existence of the Secure Capsule on the endpoint device, and the use of the secrets and/or biometrics by the Web Server is all that is required for authentication of both the device, and the user on the device. Circle-of-Trust provides a mechanism to step-up to human-in-the-loop identity verification whenever needed.
What will YOU do with Circle?
We ourselves are learning more each day about new things that can be done with Circle's remarkable architecture. These are the areas of functionality that are available for developers to develop and implement with Circle API today. Over the next months and years, we will continue to expand both its capabilities and ease of use as we work with you. If you have needs, requirements - or just ideas - that you think Circle would meet, please do contact us for a free consultation.