When you want multiple levels of validations
Circle-of-Trust™ Level 2 adds a new breakthrough, spoof-proof method of identity verification + authentication that is cryptographically fused to device authorization. At the highest level of security configuration and checks, it can even block access and attacks from compromised devices.
Circle-of-Trust™ Level 2 operates entirely within Circles that are encrypted with AES 256, without any external avenues for attack. We are implementing this first, a turn-key hosted solution in order to ensure the integrity of the methods and system. After that is released, we intend to then package API hooks and guidance that would enable developers to implement their own variations on the method, while ensuring the security integrity of the system is maintained.
Highlights:
- All operations are performed within AES 256 encrypted Circle, with no external certificate authority or exposure.
- Impervious to external attack or manipulation.
- Can be applied to protect application and device functions, not just data.
- Any level of authentication can be defined:
- N number of trusted peers
- sequenced steps / workflows
- visual confirmation
- proximity-based confirmation
How It Works
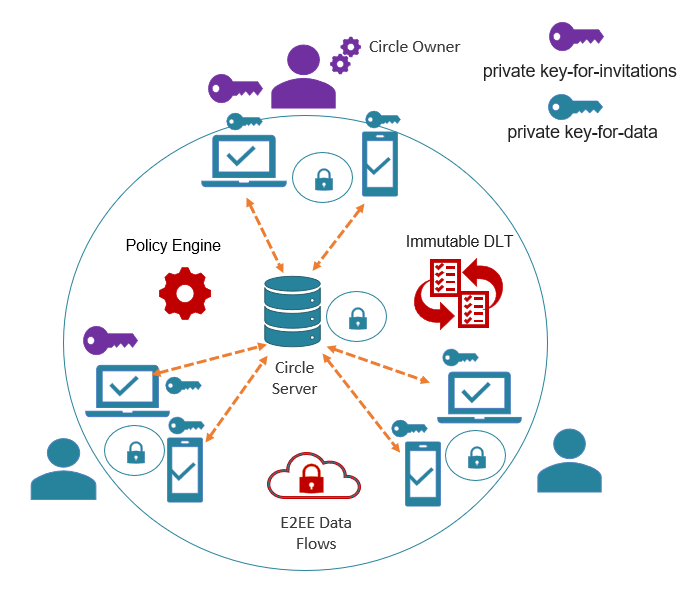
This diagram provides a high level overview of the principles and mechanisms that make Circle-of-Trust work.
Internal User Concept, DB & functionalities
- Tracking individual users as known persons, whose identity is verified by other peers in a Circle-of-Trust.
User Identity Verification, Authentication and Device Authorization
- Peer mediated identity verification, cryptographically fused to device authorization with no external authority or exposure of users or metadata in the Cloud.
Additional Device-Based Security Options
- Device PIN, Biometrics, User Challenges, Proximity-based, etc.
Policy Engine
- Enables the CoT owner to set the rules by which users who are invited and governed by the CoT must be authenticated, and their devices authorized.
- Policy Enforcement is internal to Circle and impervious to external attack or manipulation.
Internal Immutable Distributed Ledger
- Maintains an immutable record of all actions for audits, compliance & investigations.